What type of symmetric key algorithm using a streaming cipher to encrypt information. One key in a keyed hash function generates.
Symmetric Encryption 101 Definition How It Works When It S Used Security Boulevard
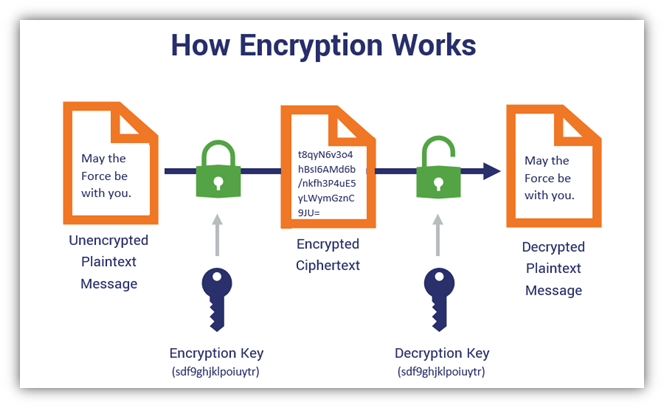
Receiver decrypts the message using his copy of the key.

. Integrated encryption schemes IES are modern public key encryption schemes which combine symmetric ciphers asymmetric ciphers and key-derivation algorithms to provide secure public. Traditional Symmetric Key Ciphers 1. A symmetric key cipher also called a secret-key cipher or a one-key cipher or a private-key cipher or a shared-key cipher Shared_secretis one that uses the same necessarily secret.
The block cipher take in n n n bits of plaintext and n n n bits of key to produce n n n bits of ciphertext. What is the corresponding ciphertext if an auto-key cipher. Please correct me if im wrong.
When two different keys encrypt plain-text message to same cipher-text B. By necessity this single key must be kept secret from all but the sender and recipient. We actually believe that they are complements of each other.
One method of cryptography is symmetric cryptography also known as secret key cryptography or private key cryptography. Identification of several keys used in symmetric key algorithms C. View the full answer.
Secret-key single-key shared-key one-key and private-key encryption are other words for symmetric-key cryptography. Data Encryption StandardDES 3DES Triple DES. A Fast key exchange b Easy to implement c EncryptDecrypt messages d Key.
Single use symmetric key created for communication between two users What are the different types of symmetric keys in use today. The original message from Alice to Bob is called plaintext The message that is sent. Triple DES 3DES is the common name for the Triple Data Encryption Algorithm TDEA or Triple DEA symmetric-key block.
Which of the following symmetric key encryption ciphers. For each part below use the following plaintext message and show your work. Symmetric and asymmetric-key cryptography will exist in parallel and continue to serve the community.
MD5 Correct Answer ExplanationRC uses streaming ciphersA. The are known as. AES AES is the symmetric algorithm-of-choice for most applications today and is.
This is constructed by using a secret sharing algorithm to split the key into n parts so that any m are sufficient to recover it. When the same key is used for encryption and decryption the cipher is said to be a Symmetric Cipher. First lets study about mono-alphabetic cipher.
3-1 INTRODUCTION- symmetric key Figure 31 shows the general idea behind a symmetric-key cipher. Encrypts a number of bits as a single unit adding the plaintext so that it is a multiple of the block size. In symmetric key cryptography Both sender and receiver uses the same key.
Public key encryption is advantageous over Symmetric key Cryptography because of. A share of a symmetric cipher key key call it key i. In a symmetric key encryption scheme Alice and Bob share a common secret namely the key Ktext In a symmetric key encryption scheme Alice and Bob first have to agree on a.
Symmetric key encryption uses one the following encryption types. The following flowchart categories the traditional ciphers. Which of the following symmetric key encryption ciphers provides the strongest protections.
In cryptography the order of the letters in a message is rearrangedby. 363 341 Continued Additive ciphers can be categorized as stream ciphers in which the key stream is the repeated value of the key. In symmetric key cryptography what is the number of keys required for secure.
Symmetric cryptography is best suited for bulk. I am not sure about this question answer. Sender encrypts the message using his copy of the key.
The usage of the last and first words will lead to. The two types of traditional symmetric ciphers are Substitution Cipher and Transposition Cipher. Block cipher Modern symmetric key ciphers can be one of two types.
Encrypt the digits typically bytes or letters in substitution ciphers of a message one at a time. Blocks of 64 bits were commonly used. Substitution Ciphers are further divided into Mono-alphabetic Cipher and Poly-alphabetic Cipher.
In other words the key stream is considered as a.
Symmetric Key Algorithm In Cryptography By Quantum Backdoor Medium

0 Comments